Description
The first file is a 32-bit Windows executable that contains a Cobalt Strike Beacon, This executable file uses two local thread storages to conceal its main functionality, evade detection, and make its code more complex and difficult to analyze, also the file contains a malicious implant known as a Cobalt Strike Beacon, which is designed to persist on a compromised system and establish communication with a command-and-control (C2) server, The Beacon periodically checks for additional commands from the C2 server that it can execute on the compromised system,The second file is a 32-bit Windows executable that belongs to the ransomware family, This executable employs some advanced techniques to make it difficult to analyze dynamically and statically, Once the malware is executed, it will initiate a series of file encryption operations using symmetric keys, To make it challenging to recover the files, the malware encrypts each directory with a different key.
URLs ( 2 )
-
http://mbrlkbtq5jonaqkurjwmxftytyn2ethqvbxfu4rgjbkkknndqwae6byd.onion
-
http://k7kg3jqxang3wh7hnmaiokchk7qoebupfgoik6rha6mjpzwupwtj25yd.onion
Analyzing sihost.exe
the Cobalt Strike beacon was identified employing the deceptive name “sihost.exe” to obfuscate its presence and appear legitimate. It’s essential to note that “sihost.exe” is a genuine Windows process responsible for managing graphical elements in the Windows interface.
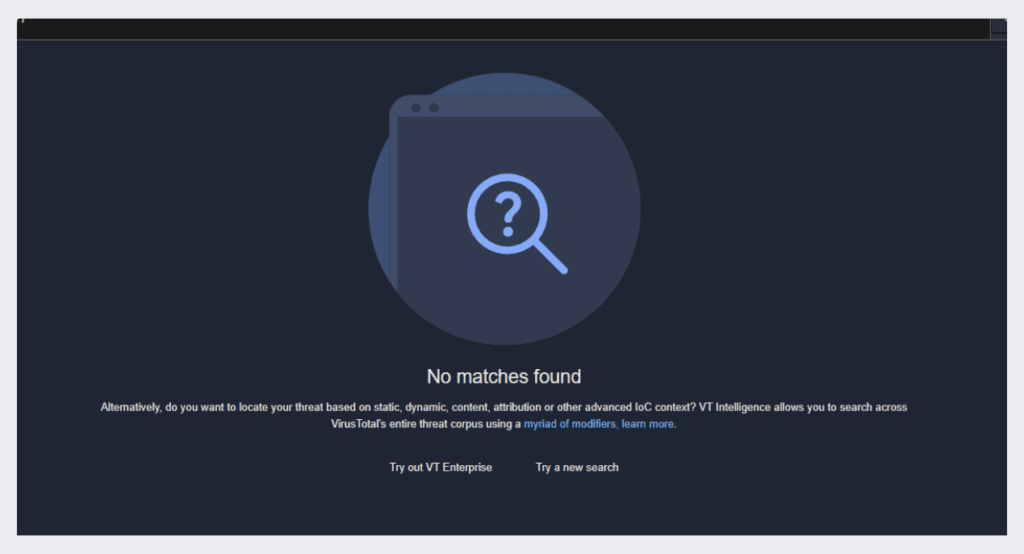
The malware has never been submitted to VirusTotal, This could suggest that it is part of a targeted campaign
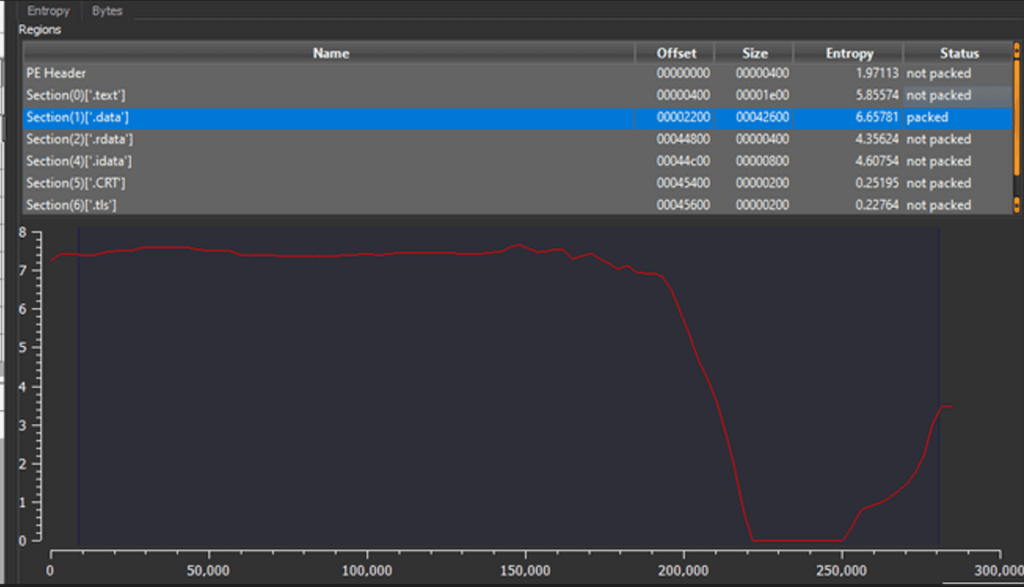
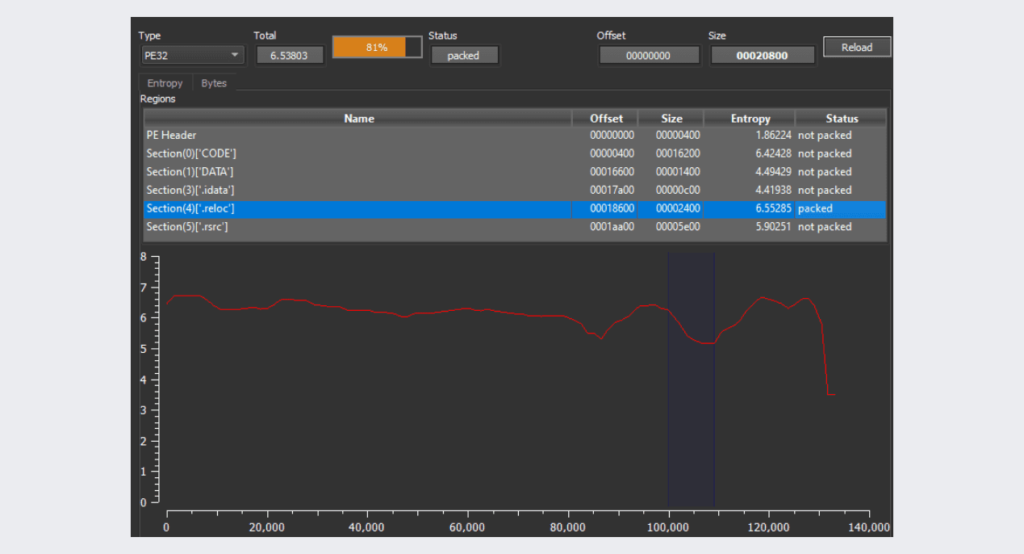
The malware data section is packed
The malware utilizes two local thread storages to conceal its primary functions, evade detection, and complicate its code, making it more challenging to analyze or debug, as the malware will execute before the main thread
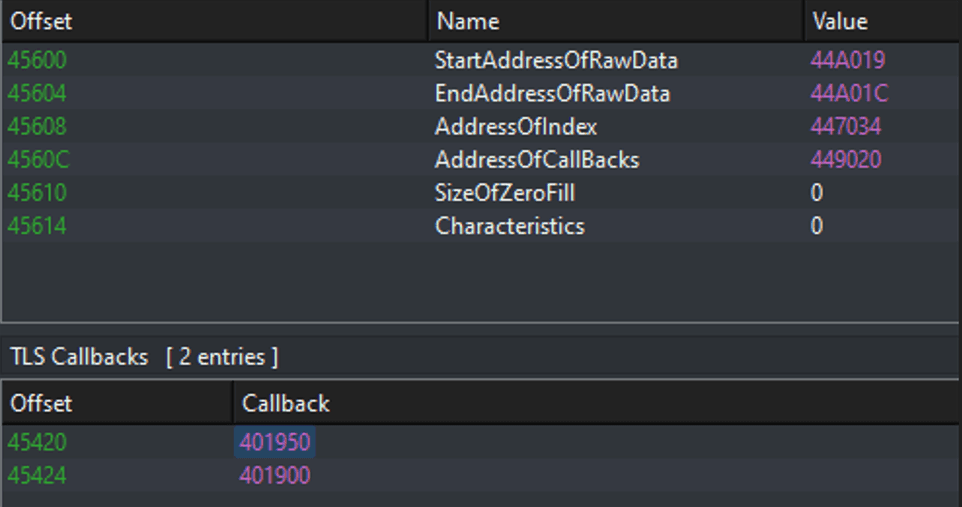
The local storage threads in this malware load mingwm10.dll for TLS management, followed by obtaining two functions __mingwthr_remove_key_dtor and __mingwthr_key_dtor using GetProcAddress(), Both functions are responsible for managing the thread-local storage.
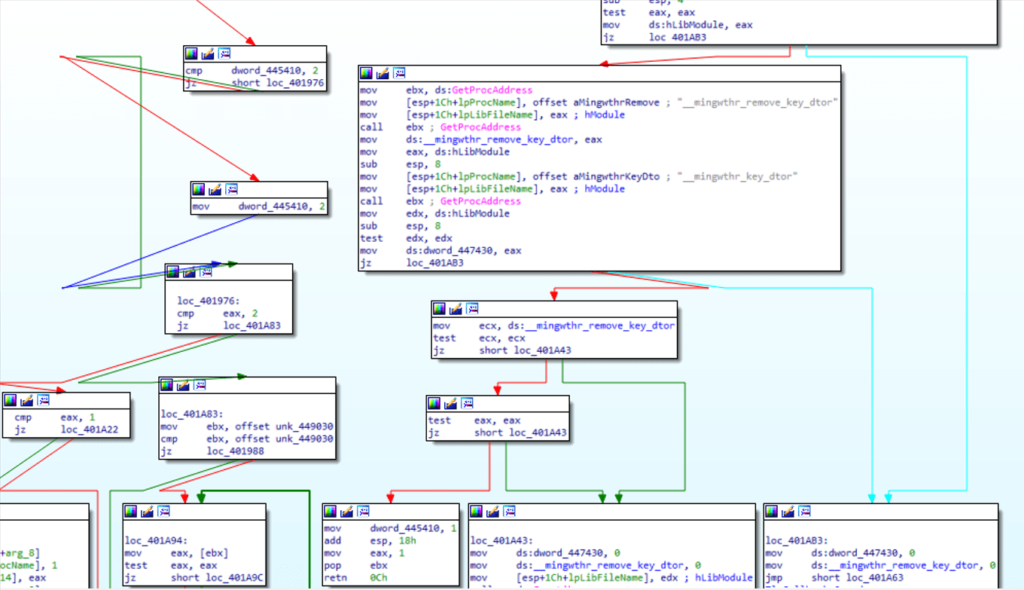
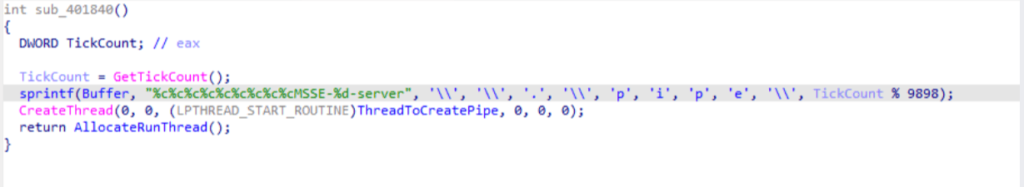
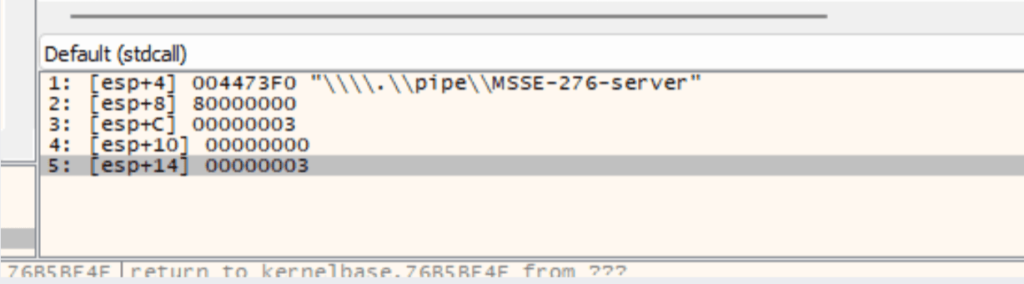
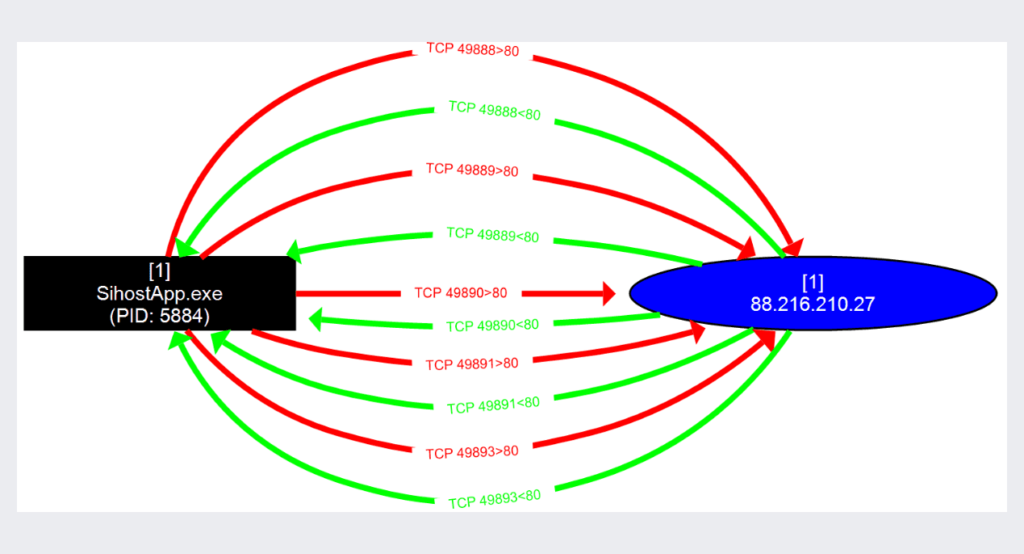
After the malware reaches the main function, it generates a random number using the GetTickCountfunction. This number is then used to create a named pipe by formatting a string using the sprintffunction, followed by creating a thread to create the pipe.
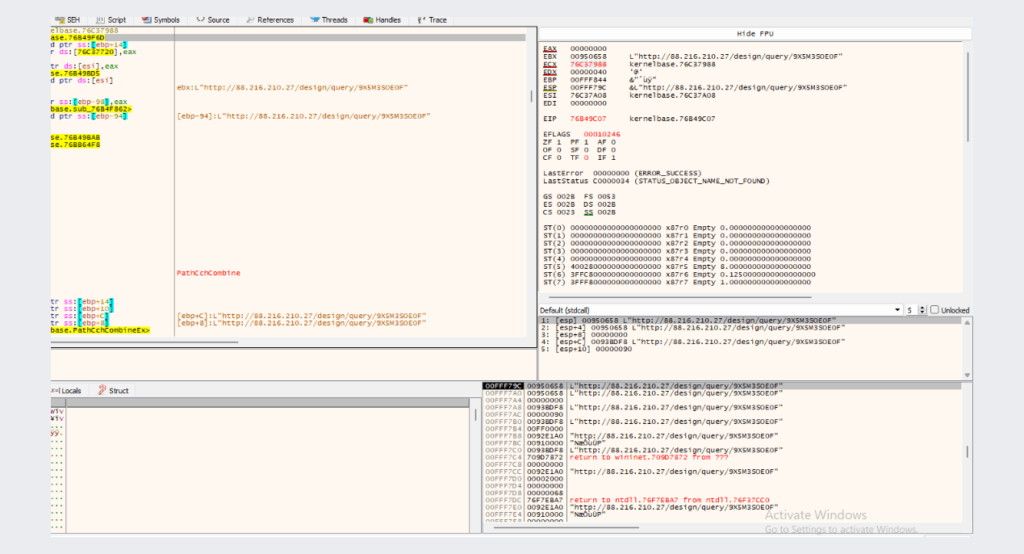
then the malware will decode the C2 function address and execute it
a diagram illustrating the flow of the Cobalt Strike Beacon
Analyzing PLAY.exe
Also for this file using the file hash to search in VirusTotal, we could not find anything, which means that the malware has not been uploaded
The malware reloc section is packed
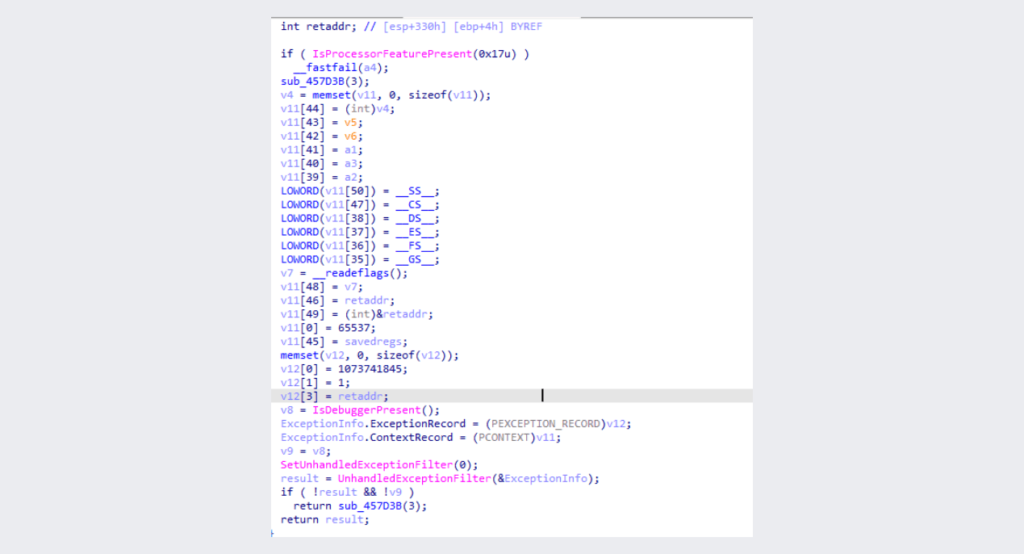
The ransomware uses a lot of anti-analysis techniques to prevent dynamic or static analysis
Once the malware executes it starts enumerating all files on the hard drive, Then, the ransomware iterates through all directories in those drives using the FindNextFileWAPI.
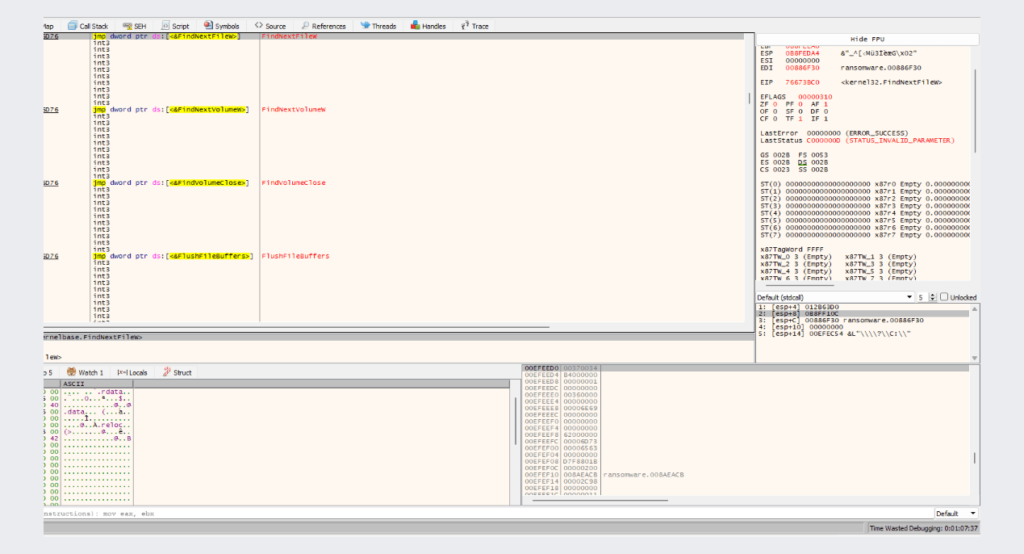
and for each directory, it will spawn a thread to encrypt all files in it, to speed up the encryption process
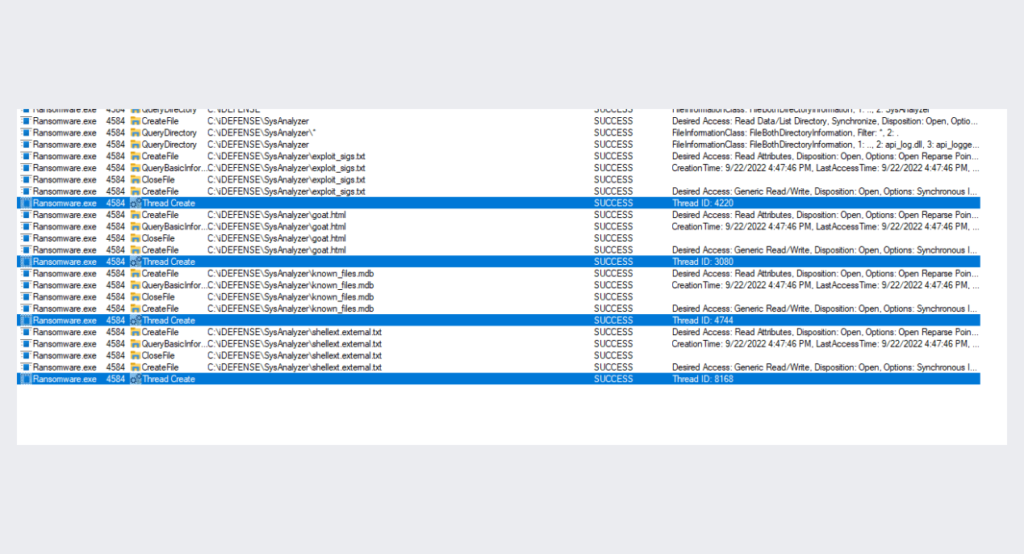
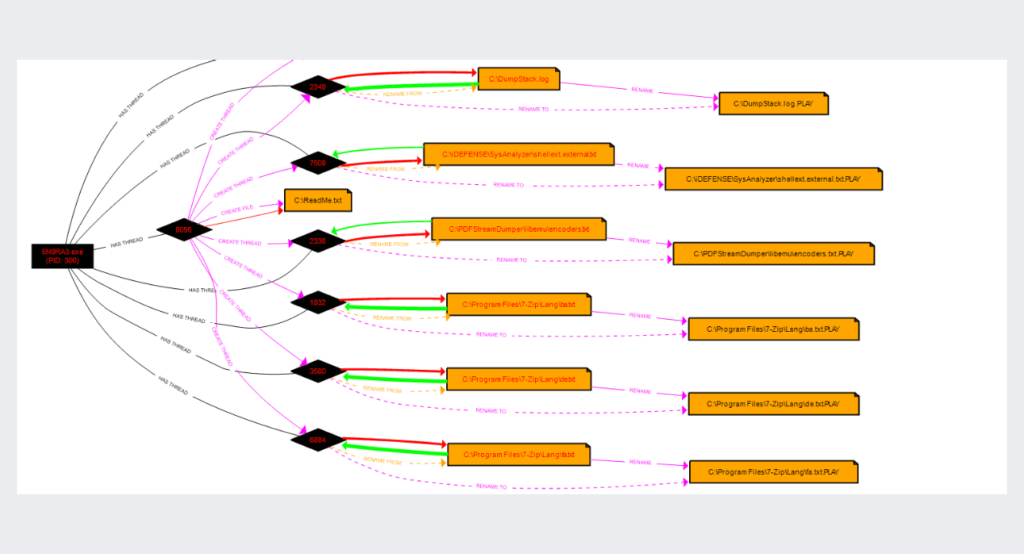
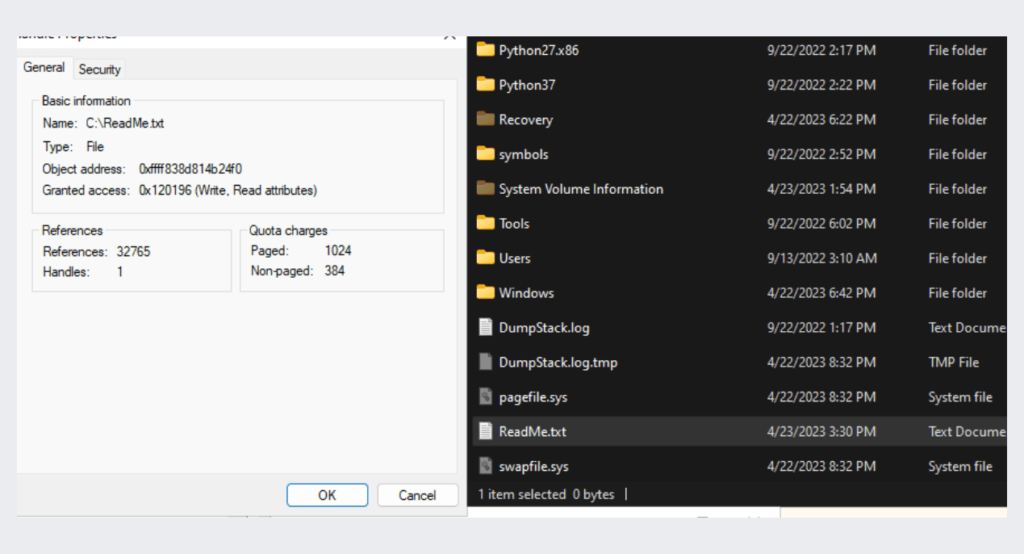
a list of large handles that ransomware opens to files and threads during its encryption process
after enumerating all files and opening a handle to them,the ransomware calls BCryptGenerateSymmetricKeyfunction that creates a key object for use with a symmetric key encryption algorithm.
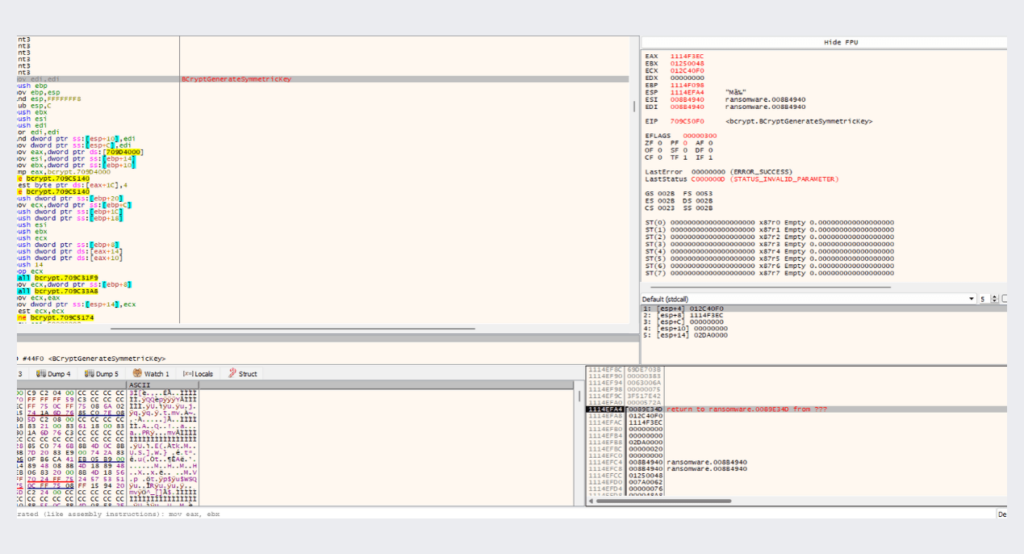
Then, it uses that symmetric key to encrypt the buffer retrieved from the files
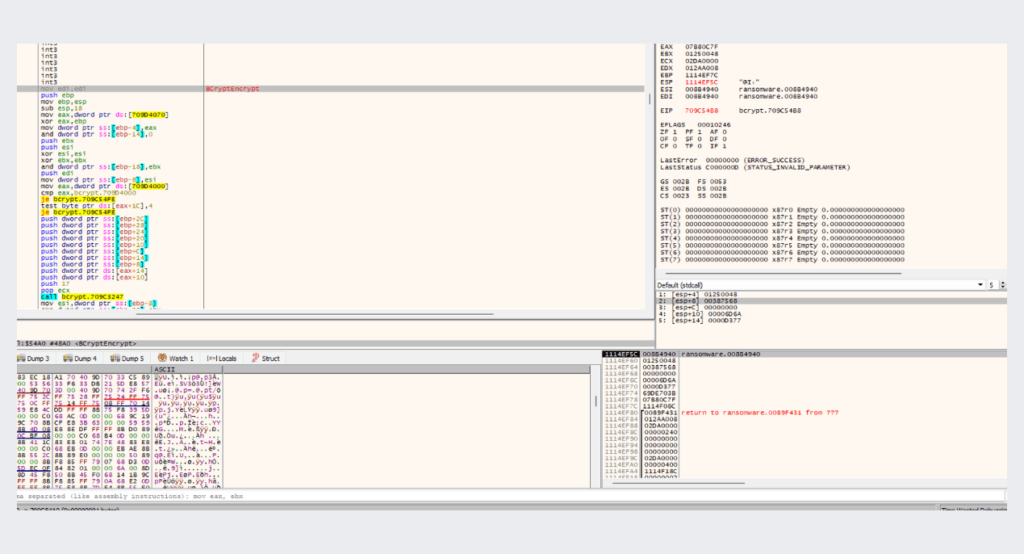
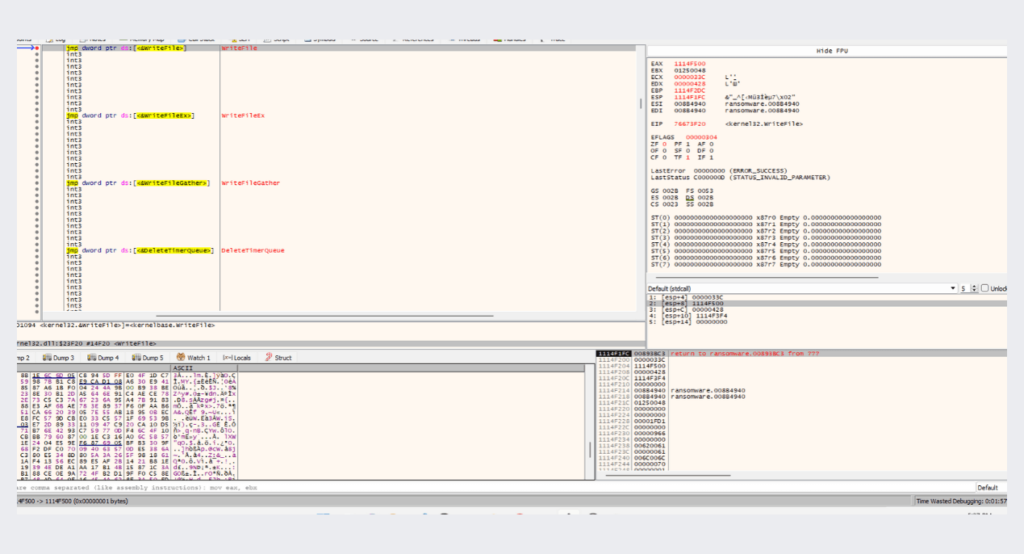
after encrypting the buffer, the ransomware writes it back to the file, causing the original buffer to be overwritten
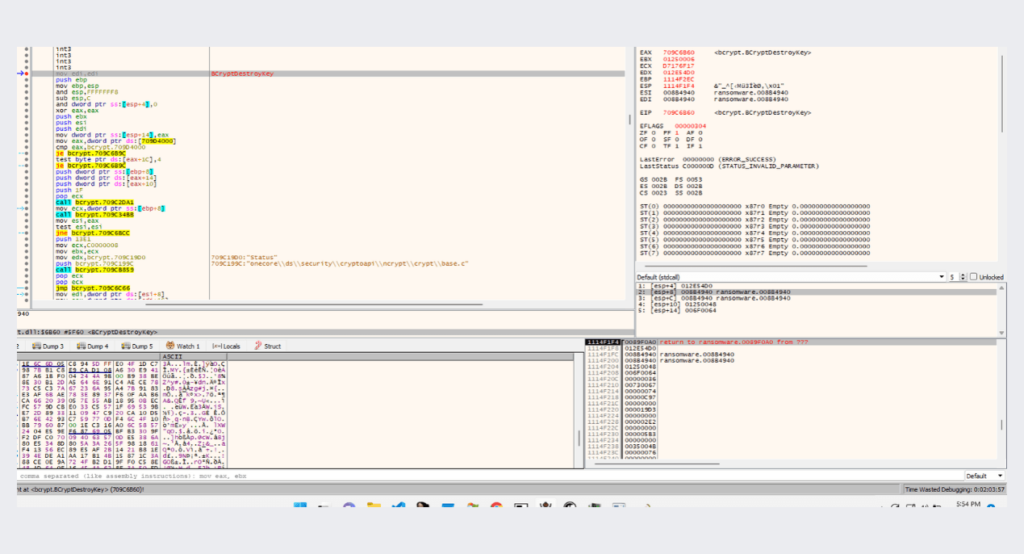
then the ransomware destroys the key from memory using the BCryptDestroyKeyAPI, making it extremely difficult, if not impossible, to recover the key data, This API securely deallocates the key object and any associated memory, which typically involves overwriting the memory with zeros or random data to prevent any residual information from remaining
The ransomware repeats these steps with all the other directories, it generates a key, encrypts all files in that directory, destroys the key, and then moves to the next directory, every directory is encrypted with a different key, and it seems that the purpose of this malware is only data destruction
Ransom Note :
the ransom note placed in the hard drive location the being encrypted
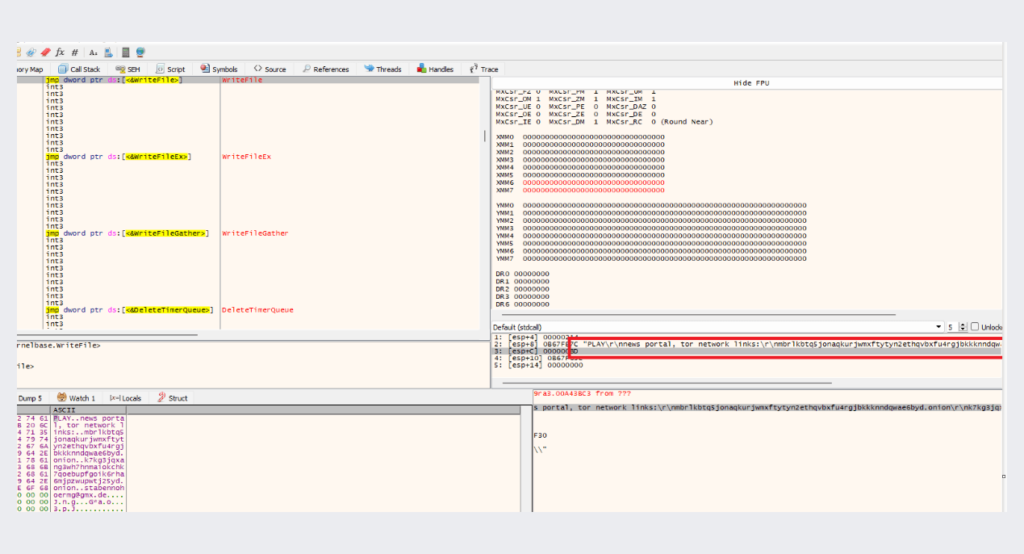
ransom note
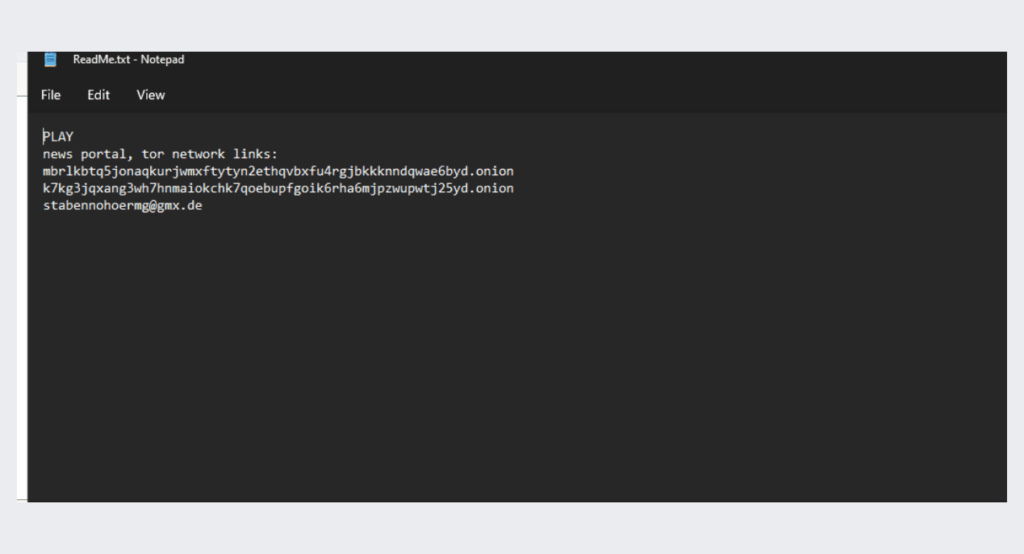
the content of the ransomware note
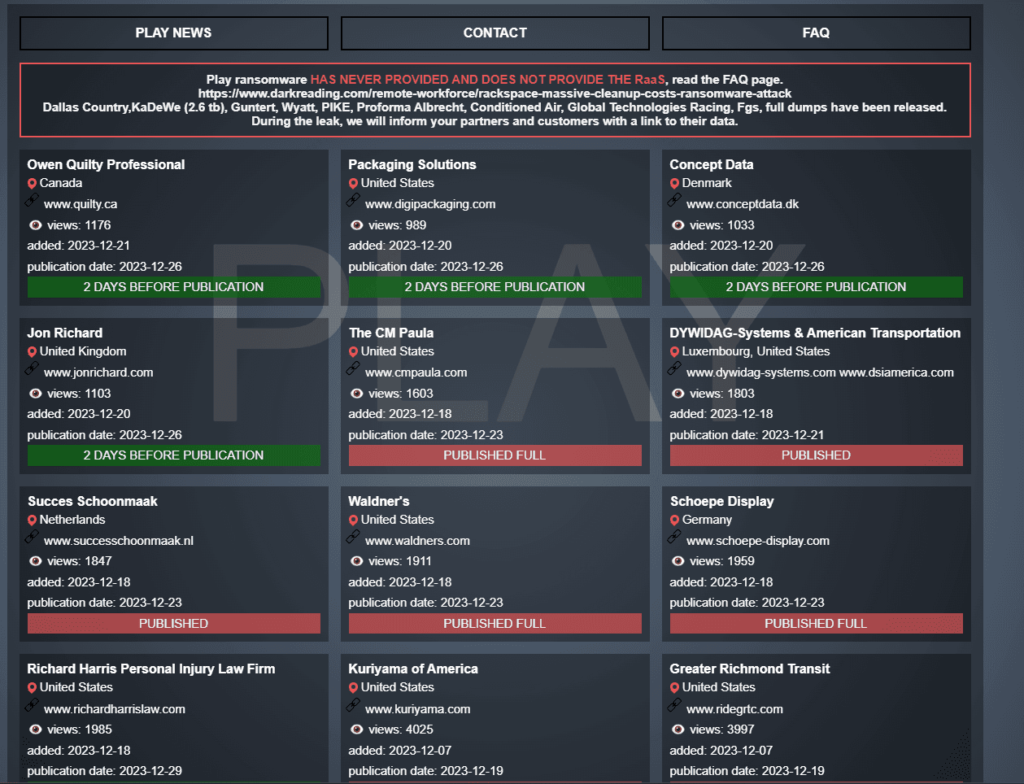
The onion site of the threat actor shows multiple affected companies being demanded a ransom, otherwise, the data will be published
a diagram illustrating the ransomware encryption flow