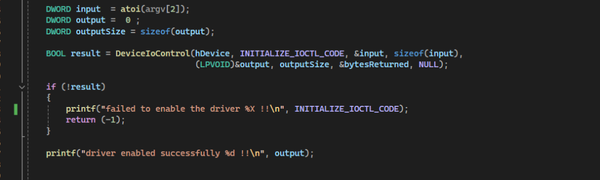
Hacking Games for Fun and Profit
While chilling in a voice chat, one of my friends suggested we play Chained Together. If you haven’t tried it, it’s a game on Steam where all players are literally chained together, and you have to climb up without dragging each other down. Sounds simple, right? Yeah… not