CVE-2025-68921: Local Privilege Escalation Affecting Millions of Gaming Laptops
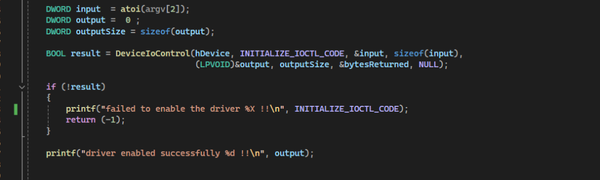
Summary This write-up details a local privilege escalation vulnerability that I reported to Lenovo PSIRT in January of last year. The issue affects an audio enhancement software pre-installed on many gaming laptops, including Lenovo Legion, IdeaPad Gaming, MSI, Thunderobot, and others. The vulnerability was tracked by Lenovo PSIRT as LEN-18785