CVE-2025-26125: Turning DoS into Privilege Escalation

As always, while surfing X (formerly Twitter), I came across an interesting tweet from vx-underground that immediately caught my attention:
"Shoutout to the homies at IObit Malware Fighter. Their IMFForceDelete driver is so wildly vulnerable, and poorly written, you can have their driver arbitrarily delete any file on the machine with 0 privileges and literally 1 line of code."
Shoutout to the homies at "IObit Malware Fighter".
— vx-underground (@vxunderground) January 7, 2025
Their IMFForceDelete driver is so wildly vulnerable, and poorly written, you can have their driver arbitrarily delete any file on the machine with 0 privileges and literally 1 line of code
Thanks @_mmpte_software for sharing pic.twitter.com/urUitquHfd
At first glance, this might seem like just another arbitrary file deletion bug, leading to a simple denial-of-service (DoS) attack. But let's be honest DoS alone isn’t something cool. The real question is: can we take this further? Arbitrary file or folder deletion has been exploited before to achieve privilege escalation, and this case might just be another opportunity to do so.
In this write-up, we’ll break down the vulnerability, analyze its impact, and see if it can be leveraged beyond just deleting files. Spoiler alert: it gets way more interesting :) .
Understanding MSI Installer
Before diving into the vulnerability itself, let's take a moment to understand a key Windows component: the MSI Installer and its rollback mechanism.
MSI (Microsoft Installer) is the standard Windows framework used to install, update, and remove software. One of its key safety features is the rollback mechanism, which ensures system stability in case an installation fails.
When an MSI package installs or updates a program, it may need to replace or modify existing system files. To prevent corruption if something goes wrong, Windows first creates backup copies of these files and stores them in a hidden system directory
C:\Config.Msi
This folder holds rollback-related files, including:
- RBF (Rollback File) – Backup copies of files that might get modified during installation.
- RBS (Rollback Script) – A script that tells Windows how to restore these files if something goes wrong.
The catch? The files inside C:\Config.Msi have random names, meaning their exact paths aren't predictable in advance. This randomness is meant to prevent tampering, but as we'll see later, there are ways around it.
If the installation is interrupted or fails, Windows will use these rollback files to restore the previous state. However, if an attacker can delete or manipulate them, this mechanism could potentially be abused for privilege escalation.
Now that we have this background, let’s take a closer look at the IObit Malware Fighter vulnerability and see if it can be leveraged for more than just file deletion.
IMFForceDelete123 driver
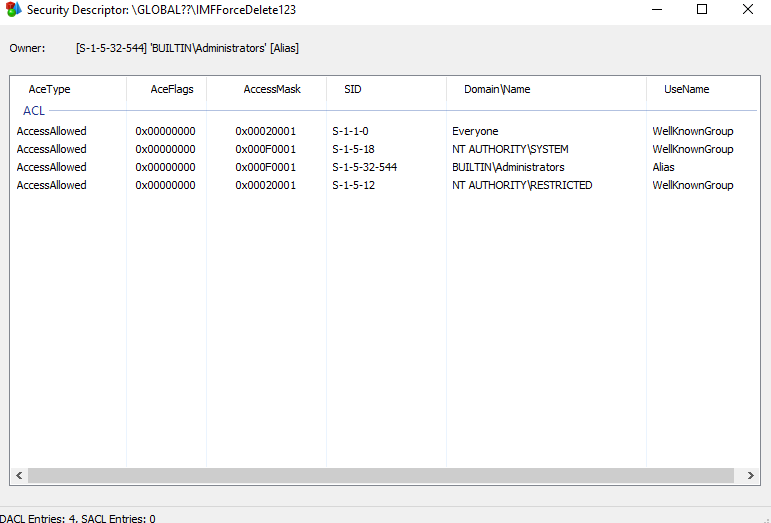
The IMFForceDelete123 driver is a kernel-mode driver and due to the absence of a properly configured Security Descriptor Definition Language (SDDL) on the device object a non-admin users can interact with it.
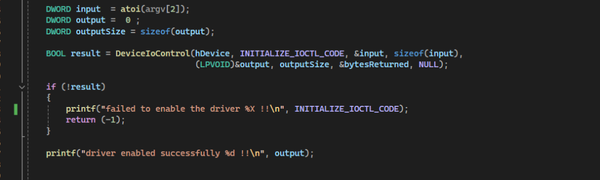
The driver recieve an IOCTL with a file name. Then the driver performs an I/O operation, and marks the file for deletion by setting specific flags. After completing the necessary operations, the driver closes the file handle, which triggers the deletion of the file or folder.
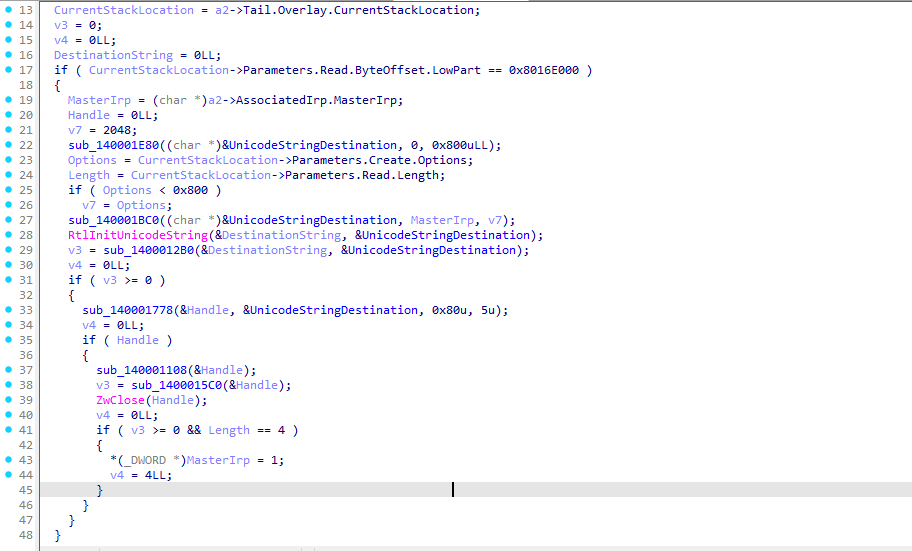
Putting It All Together
We start by installing the MSI, which drops the dummy.txt file to a location we can write to. Since the MSI is UAC compliant, a non-admin user can install it. During the uninstall process, the uninstaller moves the dummy.txt file to C:\Config.Msi, renaming it with a randomized .rbf extension. We monitor this event and wait for the .rbf file to be fully written.
Before replacing the .rbs and .rbf files, we trigger the deletion of C:\Config.Msi. At this point, we use the IMFForceDelete driver to manipulate the folder, recreating it with a weak DACL. This weak DACL allows us to delete, move, or overwrite files within the folder.
Once the folder is deleted, we replace the .rbs file with a malicious version and drop a malicious .rbf file into the MSI folder. These files will be used when the rollback process is triggered.
Finally, we signal the rollback event, causing the system to consume the malicious .rbs and .rbf files, executing the attacker-controlled code with SYSTEM privileges.
This technique is well explained in the ZDI article 'Abusing Arbitrary File Deletes to Escalate Privilege and Other Great Tricks.' I recommend reading it for more in-depth insights
fyi the MSI installer has a well-documented history with SandboxEscaper exploiting a similar bug called InstallerBypass in 2019 where it was dropped as a 0day.
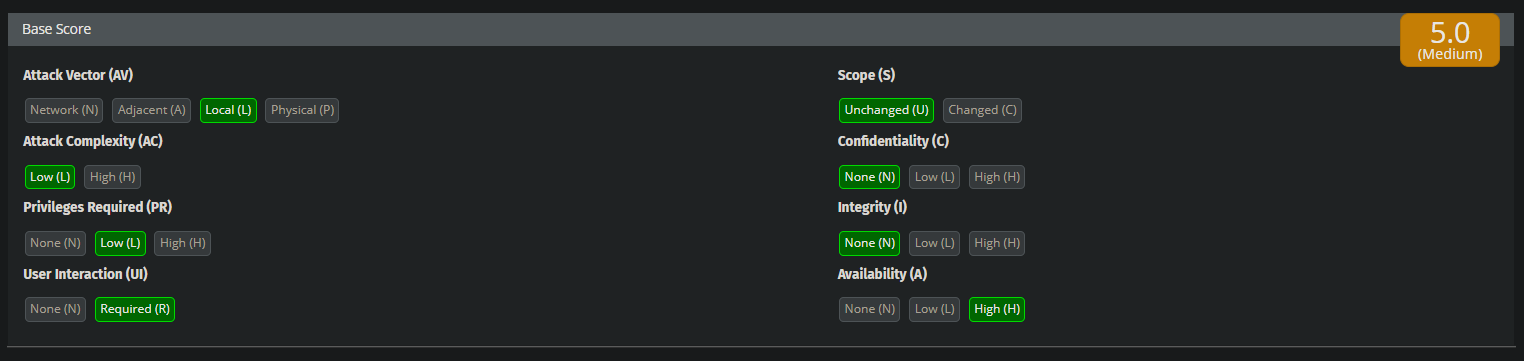
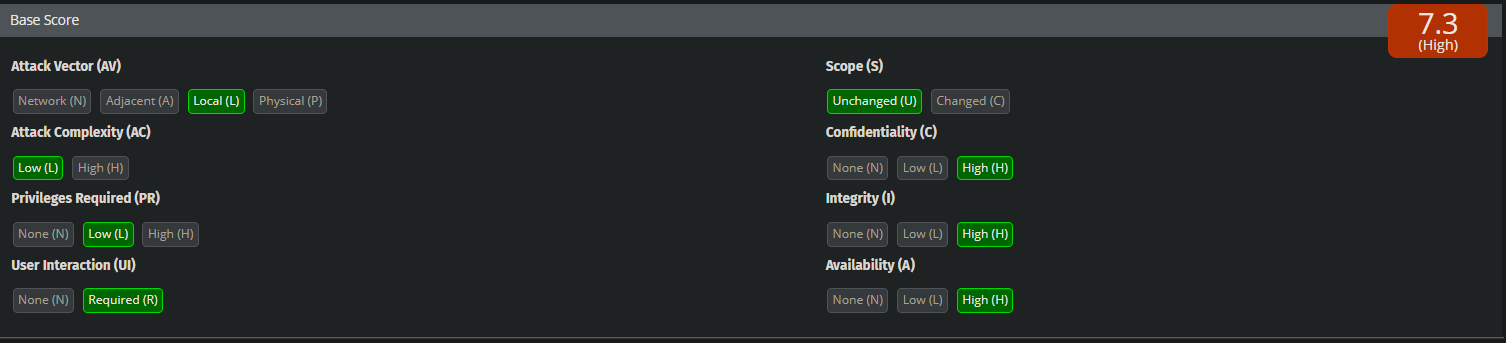
Now we are able to escalate a DoS vulnerability with a CVSS 3 score of 5 (Medium) to 7.3 (High).
PoC
PoC source code